From Log to Block: Auto-Blocking External Threat Sources with PAN-OS
A production pattern: tag external source IPs on meaningful denied threats, feed those tags into a Dynamic Address Group, and enforce a high-priority global block rule.
The problem
Internet-facing services attract constant hostile traffic. Even when traffic is denied, repeat offenders create noise and overhead: repeated sessions, repeated inspection, repeated log volume.
The design pattern
- Threat log forwarding filter matches denied medium/high threat events from the outside.
- Tagging action applies a tag to the source address at log time.
- Dynamic Address Group (DAG) matches any IP with that tag.
- High-priority security policy drops traffic from that DAG to anything.
1) Log forwarding filter (Threat logs)
Create a log forwarding profile match list for Log Type: threat and filter for real, actionable abuse.
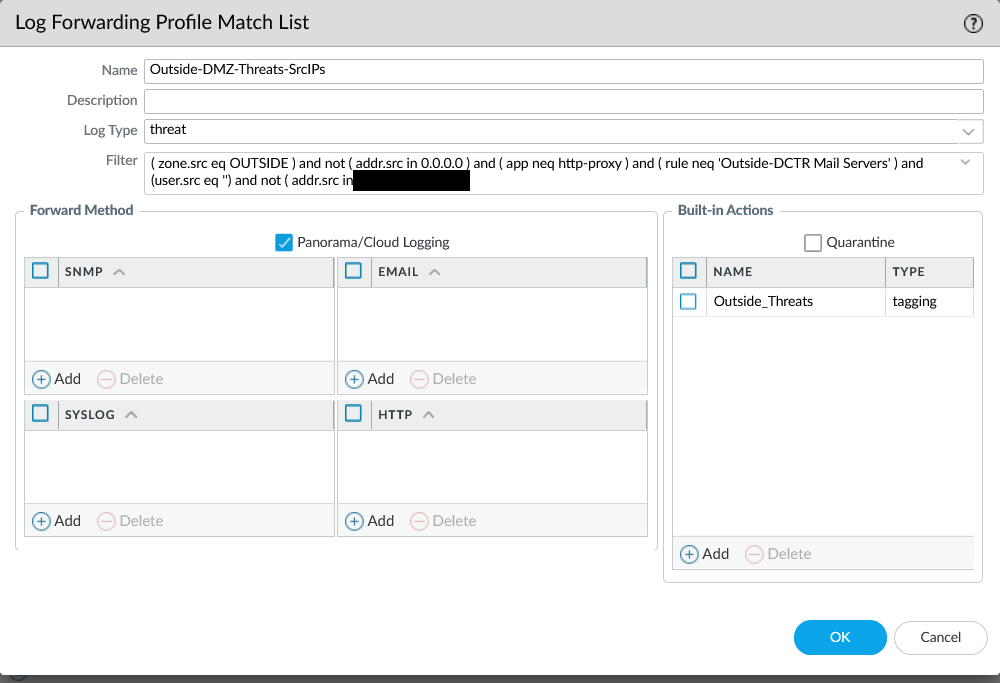
- Source zone = outside / untrusted
- Action = denied / dropped (based on your logging model)
- Severity = medium/high (tune for your environment)
- Exclude known infrastructure and expected traffic patterns
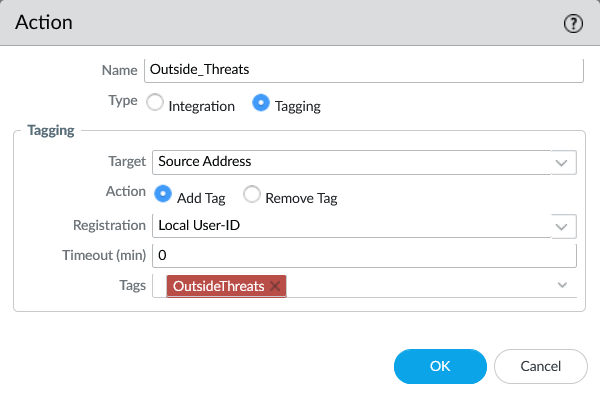
2) Tag the source IP (built-in tagging action)
The built-in action tags the Source Address (not a user, not a destination). The firewall observes an event and immediately turns it into an enforcement input.
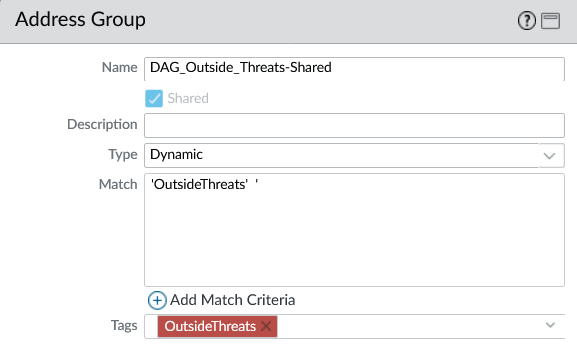
3) Dynamic Address Group (DAG)
Define a Dynamic Address Group that matches on the tag. As soon as the firewall registers the tag, that IP becomes a member of the DAG.
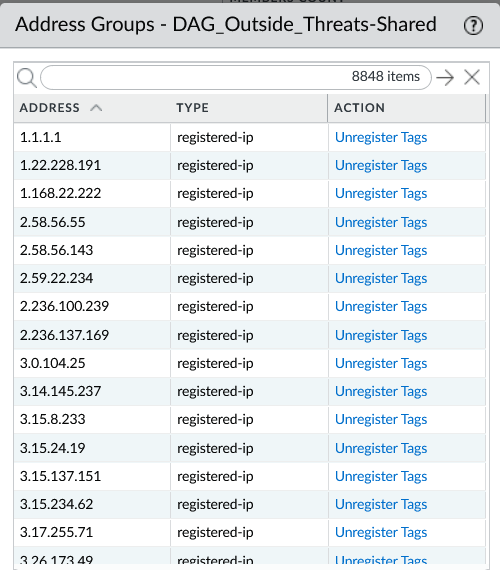
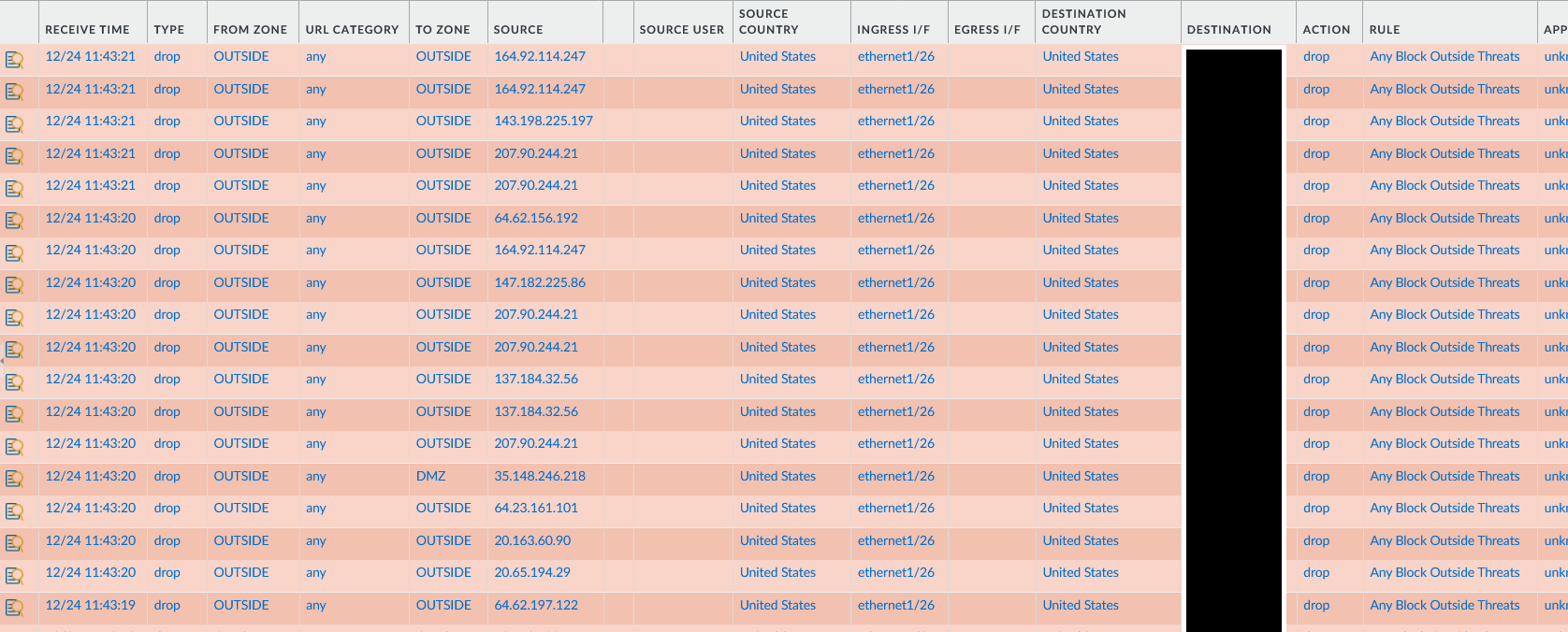
4) Confirm it’s populating
Once tags start being applied, the DAG should fill quickly — especially if you’re protecting public IP space.
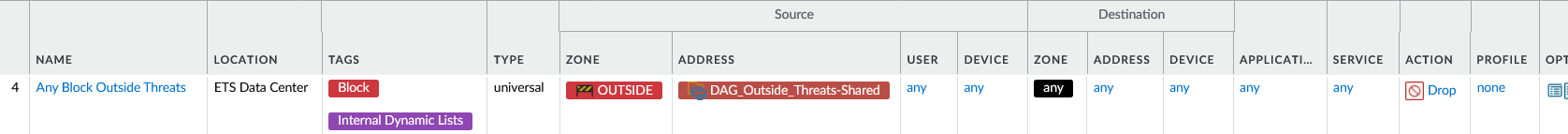
5) High-priority block rule
Place a high-priority security rule near the top of the rulebase to drop traffic from the DAG to anything.
What this buys you
- Noise reduction: repeat offenders stop generating meaningful churn after the first hit.
- Performance protection: known-bad sources get dropped early.
- Self-updating enforcement: no manual lists, no external EDL hosting, no scripts required.
Guardrails
- Exclusions matter: don’t tag your own infrastructure, trusted scanners, or known 3rd-party services.
- Severity threshold matters: medium+ works well in many environments, but tune aggressively.
- Tag lifecycle matters: decide whether tags age out or get cleared manually.
- Placement matters: keep the block rule high so it acts as an early containment gate.
This post describes an operational pattern (“how to think”). Implementation details should be tested safely in your environment.